This three-part series focuses on the security of, and strategic competition around, fiber optic communications infrastructure – the data super-highways of our world.
Part 1: What is the optical core and why is it important?
Part 2: The impact of strategic competition on fiber optic infrastructure markets
Part 3: How the US and its partners can ensure the security of the optical core
Over 99% of the world’s intercontinental communications travels along an estimated 570 submarine cables crisscrossing the planet’s seabed. These submarine networks, spanning over 1.4 million kilometers, underpin global communications.
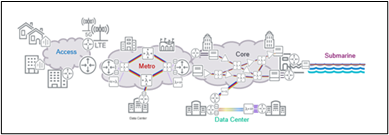
Modern submarine cables function through the technology of fiber optics, where information is transmitted by coherent laser-based modems through very thin glass fiber cores. Each fiber can carry tens of terabits of data per second. Fiber optic amplifiers, referred to as repeaters, boost these optical signals every 60-70 kilometers when transmitted over long distances. When a subsea fiber optic cable is laid, it connects two or more landing points. Upon reaching these landing points, the cables connect to terrestrial backhaul networks.
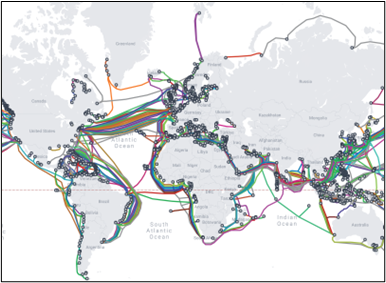
On land, the internet backbone is also enabled by fiber optics, commonly referred to as the optical core. Despite their significance, submarine and terrestrial networks tend not to resonate in public consciousness, especially in comparison to satellites and the more visible parts of terrestrial networks such as cell towers. Tangibility aside, cables offer higher capacity and lower latency when compared to satellite communication, meaning they can transmit far more data with increased reliability. These benefits are increasingly important given the exponential growth of global data usage. International bandwidth demand has grown by 33% annually over the past 5 years.
Historically, these cables were developed and owned by telecommunication company companies and consortia. As the internet developed, private investment in fiber optic infrastructure grew, with major investment now being led by content delivery providers, hyperscalers, or investor groups. When it comes to submarine cable maintenance, a consortium of owners will contract repair services to third-party entities. Consideration of location, ownership, and maintenance of the optical core on land and on sea is important, especially as the majority of diplomatic and military communication around the world passes through these cables. In fact, the existence of military-operated and classified cables is minimal.
Security Risks
Given the existential global reliance on optical infrastructure, it is a vulnerable target for surveillance, sabotage, and disruption - whether by nation states or substate actors, and for economic, geopolitical, or military purposes. When it comes to submarine cables, which can pass through several maritime jurisdictions and international waters, transnationalism necessitates robust awareness of local jurisdictional law, especially around mandated data access by government and law enforcement.
When considering the risks around optical core infrastructure, we will utilize the traditional information security triad of confidentiality, integrity, and availability.
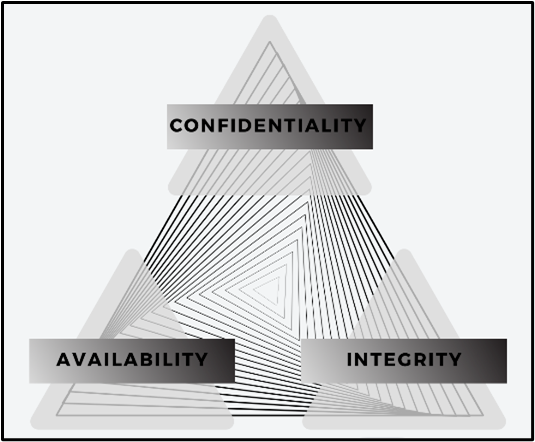
Confidentiality
Securing the confidentiality of data in transit is critical. Fiber optic cables transmit data via light, making it difficult for unauthorized individuals to intercept the data but not impossible. A British Government Communications Headquarters (GCHQ) tapping operation was revealed in the 2013 Snowden Disclosures. The 1971 US government efforts around Soviet telecommunication cables, known as Operation Ivy Bells is another example. These days, optical fiber can still be ‘tapped’ using commonly-available equipment, although modern transmission methods have made this more difficult. By bending the fiber, it can be possible to reflect the light being pulsed through it, a concept known as evanescent wave coupling. The identification of potential intrusions, while difficult, can be done by monitoring the light intensity and looking for any anomalous fluctuations. Such detection relies, however, on network vendors having both the technical capability to identify anomalies and the motivation to report them.
As is the case with most data transfers today, encryption is widely used in optical core infrastructure. Encryption can mitigate the impacts of snooping, but even without the ability to decrypt data, adversaries could access information such as the origin and destination of traffic. Foreign decryption efforts remain zealous, and as quantum computing looms on the horizon, consideration should be given to the development of post-quantum cryptography. Meanwhile, information that is captured today can be stored and decrypted once quantum computing is powerful enough to implement Shor’s Algorithm (“harvest now, decrypt later”), which poses a risk to information that must be kept confidential for an extended period of time, such as classified materials.
Integrity
The integrity of the information being transmitted across fiber optics is not guaranteed. Devices can be inserted into the cable to manipulate signals and corrupt data. A malicious actor can pretend to be a source or recipient of certain information by changing the data expectations and steering traffic off a path. Research around the use of ‘fiber fingerprinting’ to focus on this integrity risk is ongoing.
Availability
Much like any other piece of physical infrastructure, cables are vulnerable to an array of risks, including cuts, breaks, and bends. In the case of submarine cables, most cable faults are due to accidental damage (through anchoring or fishing) typically affecting one cable while natural phenomena (such as undersea earthquakes and tsunamis) affect wide regions and multiple cables simultaneously. Severing a cable can be very disruptive as deep-sea repairs can be protracted. Submarine cable landing points are uniquely vulnerable given how easily they can be reached, especially as they are often clustered together.
In January 2022, a devastating underwater volcanic eruption reshaped the seafloor and destroyed over 100 miles of the single submarine cable connecting the Pacific Island nation of Tonga to the outside world. The country was entirely offline for three days, with major disruption continuing for weeks. Repeated earthquakes in Taiwan in 2007 and 2010 led to damage of fiber-optic cables for much of the country and the broader region, disrupting service for multiple days, albeit disruption was mitigated by rerouting service on undamaged cables.
There are numerous recent examples of intentional disruption of subsea cables. In April 2022, the US Department of Homeland Security revealed details around a foiled cyber-attack on a telecommunications company involved in a submarine cable linking Hawaii and the Pacific. While this attack was attributed to an international hacker group, one would be remiss to ignore malicious state behavior around the optical core. Sabotage of submarine cables, whether physically or via a cyber-attack, can be very difficult to attribute. Recent unattributed attacks include that on a Taiwanese subsea cable in April 2023 and a Baltic subsea cable connecting Sweden to Estonia in October 2023.That these attacks occur on or around fraught geopolitical zones is likely no coincidence.
Conclusion
Recognition of telecommunications as critical infrastructure for national security interests has steadily increased over the last decade. However, the significant security risks around submarine and terrestrial cables, and specifically the optical technology they rely on, requires more explicit attention by policy makers and elected officials alike. These risks are global and will have large secondary effects. Their ripples will extend far beyond the fibers. The vulnerability of optical equipment, both on land and undersea, necessitates the adoption of trusted vendors. Given the multi-faceted nature of the use, private ownership, and vulnerabilities of fiber-optics, the effort to secure them and enable a resilient internet backbone requires international cooperation and public-private collaboration.
The views expressed in this article are those of the authors and do not reflect either way the views of Venable LLP.
Authors

Senior Director, Global Security and Technology Strategy, Venable LLP


Wahba Institute for Strategic Competition
The Wahba Institute for Strategic Competition works to shape conversations and inspire meaningful action to strengthen technology, trade, infrastructure, and energy as part of American economic and global leadership that benefits the nation and the world. Read more


Polar Institute
Since its inception in 2017, the Polar Institute has become a premier forum for discussion and policy analysis of Arctic and Antarctic issues, and is known in Washington, DC and elsewhere as the Arctic Public Square. The Institute holistically studies the central policy issues facing these regions—with an emphasis on Arctic governance, climate change, economic development, scientific research, security, and Indigenous communities—and communicates trusted analysis to policymakers and other stakeholders. Read more


Science and Technology Innovation Program
The Science and Technology Innovation Program (STIP) serves as the bridge between technologists, policymakers, industry, and global stakeholders. Read more