This three-part series focuses on the security of, and strategic competition around, fiber optic communications infrastructure – the data super-highways of our world.
Part 1: Optical Core Infrastructure: The Hidden Highways of Connectivity
Part 3: How the US and its Partners can Keep the World’s Data Super-Highways Open, Free, Reliable, and Secure.
As outlined in the first and second part of this series, the global telecommunications and geopolitical landscape has evolved over the past decade, with physical, technical and political risks to the optical core meriting greater attention from policymakers. To mitigate these risks, more needs to be done to empower trusted entities to build, maintain, and repair the optical infrastructure that keeps our internet and our world running.
Safeguarding subsea cables, now a critical global collective action issue, requires greater coordination and cooperation, both across borders and among different stakeholder groups. A comprehensive international framework for these efforts does not yet exist, in part due to the divergent interests of authoritarian nations when it comes to internet governance, but significant progress is achievable even in its absence.
Against this backdrop of increasing complexity and risk, the US Government has acknowledged the need to enhance the security and resilience of subsea cables through a dedicated workstream in the recently released US International Cyberspace & Digital Policy Strategy. This represents an important step towards a more comprehensive, whole-of-government approach.
Given the criticality of subsea cables to the maintenance of an open, inclusive, secure, and resilient digital ecosystem, however, the US should go further by developing a dedicated subsea cable security and resilience strategy. This standalone strategy would elucidate how the US Government will achieve its stated policy objectives, which federal government agencies or interagency initiatives are responsible for domestic and international activities, and how it will work with stakeholders in its implementation.
There is a clear precedent for this effort with the 2021 US National Strategy to Secure 5G and Implementation Plan and the two initiatives would likely benefit from synergies in terms of educating and engaging with international partners.
To inform this broader strategic effort, this article identifies 18 tangible steps that governments can take to advance the security of subsea cables, covering physical risk mitigation, technical risk mitigation, political risk mitigation, incident response and recovery, and global governance.
The recommendations in this article are informed by current realities, including:
- A significant increase in cable deployments in the coming years driven by increased bandwidth and increased route diversity demands;
- increased risk of espionage and sabotage in a world of heightened geopolitical tensions;
- a stated desire in Chinese Communist Party industrial policy to significantly increase the market share of Chinese suppliers;
- the limitations of existing international and multilateral institutions to address risks;
- less awareness of the geopolitical implications of cable security in comparison to the discourse around 5G security; and
-
the global governance challenges for national governments due to jurisdictional limitations, multiple national agencies with remit, outdated legislation, and ownership of the optical core infrastructure supply chain being largely private.
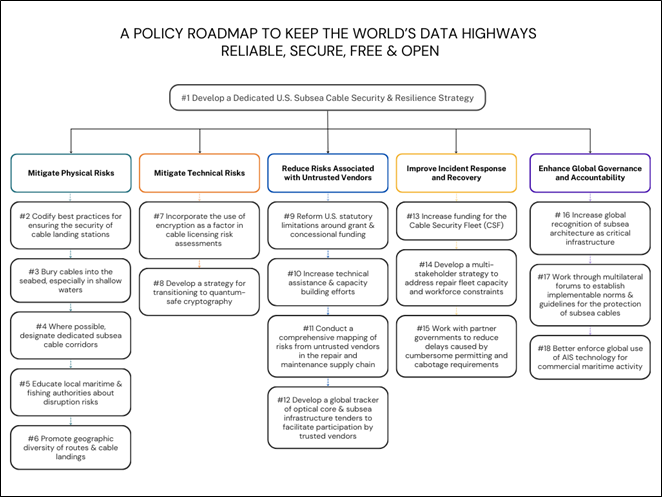
Mitigating Physical Risks
As discussed in Part 1 of this series, most accidental subsea cable disruptions occur in shallower water near shorelines. It is also where sabotage operations can be most easily conducted. Accordingly, addressing the physical security of cables and hardening cable landing stations (CLS) is a critical step for increasing resilience.
While shallow-water cables are armored and commonly buried below the seabed for additional protection from commercial fishing operations, cables at greater than 100 meters’ depth are often surface-laid. Thus, in areas near deepwater ports or areas of high shipping traffic, cables are often not buried. This lack of physical protection greatly increases the risk of accidental disruption, while creating plausible deniability for potential sabotage operations. While costly, international best practices should evolve to recommend the burying of shallow cables, where seabed conditions permit, in areas of high shipping traffic.
Secondly, there is a need to better ascertain whether disruption or damage to subsea infrastructure is accidental or intentional. As a first step, countries should establish ‘cable corridors’ - areas of high subsea cable traffic through which ships cannot travel. This will reduce the risk of accidental damage, particularly by commercial fisherman and vessel anchors, while making it more challenging to obfuscate sabotage operations. Since legacy cables were laid along traditional shipping and fishing zones, a holistic shift may not be possible, but should at a minimum be implemented for new cables.
Furthermore, countries should conduct educational initiatives with local marine and fishing authorities to highlight cable pathways, as a means to reduce unnecessary instances of disruption.
Finally, further investment and construction of subsea cables and geographically diverse, protected terrestrial backhaul routes is important for increasing redundancy. Maximizing the geographic diversity of new cable routes and landing points remains an important concept in subsea architecture because it reduces the risk of damage from any single disruptive event by enabling rerouting. Any decisions around routes, landing points, and terrestrial backhaul routes should continue to include consideration around high-risk territories of geopolitical tension, such as Hong Kong.
Mitigating Technical Risks
Today, only a small percentage of global subsea cable traffic is encrypted by the cable operators themselves, and much of the traffic across cables globally remains unencrypted. In terms of technical protections, it is imperative that operators implement robust end-to-end encryption protocols for data transmissions across subsea infrastructure. The use of optical encryption can secure data in transit in the optical transport layer of the network by transforming the data using an algorithm to make it unreadable to anyone except those possessing the key, as it is carried over wavelengths across fiber-optic cables.
The US can increase the adoption of such security best practices by incorporating them as a factor in the risk assessments conducted by Team Telecom, the US interagency group in charge of reviewing the licensing of new subsea cables. This will incentivize the private sector to invest in technical security measures for new subsea cables.
Developments in quantum computing technologies will further exacerbate the need for encryption and stronger security. Effective cybersecurity will necessitate the use of Post-Quantum Cryptography (PQC) or Quantum Key Distribution (QKD). Accordingly, the US and its partners should have a strategy for the communications sector, and critical infrastructure writ-large, to transition to quantum-safe cryptography. These recommendations are aligned with the critical infrastructure focus and goals of National Security Memorandum-10 on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems and the Quantum Computing Cybersecurity Preparedness Act of 2022.
Reduce the Risks Associated with Untrusted Vendors
Chinese optical and telecommunication vendors continue to sell products below cost, often with upwards of 30% discounts in comparison to the pricing from trusted vendors: a key driver of the adoption of telecommunications technology from untrusted vendors. The associated risks were discussed in Part 2 of this series. To reduce their prevalence, the US and its partners need a comprehensive approach to drive the procurement of equipment from trusted vendors in the global optical core.
This approach must include a focus on reducing the cost difference between Chinese vendors and trusted vendors. This can be achieved in part by enhancing access to grant or concessional financing for international optical core projects. Reforms to reduce Congressional and statutory restrictions on development financing for trusted vendors are sorely needed to allow for funds to flow more readily. Matching Chinese vendors dollar-for-dollar is not necessary, but closing the price difference is critical for persuading governments and operators in resource-constrained markets to eschew untrusted vendors.
In tandem, the US must continue to work with partner governments to raise awareness around the risks of untrusted vendors and the benefits of leveraging trusted vendors for development outcomes to drive last-mile connectivity. Technical assistance is critical to ensuring developing countries have the capacity to effectively implement and manage subsea infrastructure. The $5 million of CABLES program funding, which facilitates technical assistance and capacity building on the security of subsea cable systems, is a good start but further investment is needed.
The US and partner governments must also coordinate more closely with industry to ensure that trusted vendors are aware of tenders for key optical core infrastructure projects around the world through the establishment of a comprehensive tracker of government tenders for critical technology. The US Department of State should lead this initiative, in line with its stated objective in the International Cyberspace & Digital Strategy to “support U.S. and other trusted suppliers in the installation, operation, maintenance, and repair of secure infrastructure.”
Finally, the US and its international partners should also take steps to ensure that maintenance vessels working on cables of strategic import are not operating out of nations which could use the storage of maintenance equipment as means to conduct sabotage operations. The recent public reporting that SBSS, a company operating out of Shanghai, is one of three maintenance providers of Yokohama Zone, a consortium used by internet cable owners in the northwest Pacific, highlights this risk. As a first step towards ensuring a more trusted supply chain for maintenance and repair, the US Department of Homeland Security should conduct a comprehensive mapping exercise of the existing supply chain and where it’s reliant on untrusted vendors to provide products or services.
Multilateral efforts to shape norms and standards around subsea infrastructure are nascent but expanding. These include the recently launched Quad Partnership for Cable Connectivity and Resilience, and the Global Coalition on Telecommunications (GCOT), an informal multilateral coalition focused on promoting international alignment and innovation. The US should leverage these forums to implement the above recommendations in coordination with international partners, in order to expand the collective impact.
Improve Incident Response and Recovery
Installing, maintaining, and repairing most subsea infrastructure falls to the private-sector owners and operators of those cables. While the ships that install cables are different from those that conduct repair and maintenance, both types suffer from global capacity issues. In terms of the current commercial fleet, there are far more installation ships than repair and maintenance ships. The latter can cost between $100 - 120 million when fully equipped, and upwards of $15 million to operate yearly.
Since 2021, the US government has taken steps to enhance the fleet of vessels capable of subsea cable repair and maintenance through the creation of the Cable Security Fleet (CSF), which includes two commercially viable, privately owned United States-flagged and crewed cable vessels that have met national security requirements. Given the distances involved, as well as the often-lengthy time required to remediate disruption to subsea cables, two ships is insufficient. If the US Government wants to effectively minimize disruption, the CSF must receive additional funding to expand its capacity.
Furthermore, the commercial repair fleet itself needs both expansion and modernization, with an insufficient number of ships, many of which are 30 to 40 years old. Beyond the ships themselves, the cable fleet has a future workforce challenge, with many of the limited pool of current cable industry professionals aging out of the workforce. Likeminded governments should convene the major industry participants to outline a strategy for how the public and private sectors can collaborate to solve this workforce challenge.
On the regulatory front, overly burdensome permitting processes within many countries have led to increasing global delays for subsea cable installation and repair. These processes can often lead to regulatory backlogs of months, if not years, as observed in Malaysia and India. Most recently, inefficient permitting led to lengthy delays on the repair of Seacom’s Tata TGN-Eurasia cable in the Red Sea region following its initial outage in February 2024.
Likewise, there has been an uptick in the use of preferential cabotage rules – a protectionist measures, mandating that installation and repairs be performed only with national ships and crew. Indonesia, a country with over 60 separate subsea cables landing or passing through its territory, as well as three upcoming cables delayed by the regulation, has some of the more burdensome requirements in this regard.
The US and its international partners must engage more proactively with governments that are implementing such measures to emphasize their negative impact on the security and resilience of subsea cable infrastructure. This should be supplemented by capacity-building activities which enable partner governments to meet their regulatory objectives in a more effective manner.
Enhance Governance and Accountability
The importance of subsea infrastructure has led to its designation as critical infrastructure in domestic regulation and policy around the world. This recognition must extend into the international domain by integrating subsea cables into multilateral discussions on security and resiliency of technology.
There are already partners identifying and adhering to global security standards for subsea infrastructure. Most notably, this includes the International Cable Protection Committee (ICPC), an industry forum for cable owners and some governments. There are some international commitments around subsea infrastructure, including the United Nations Convention on the Law of the Sea (UNCLOS), which establishes maritime jurisdiction in territorial waters and exclusive economic zones but does not explicitly prohibit targeting subsea infrastructure as military targets during wartime. It should do so; however, it is unlikely that this will occur given current dynamics within the United Nations. Therefore the US should continue to work with groupings like the G7, the GCOT and the Quad to set guidelines on the security of subsea cables.
Secondly, as stated in the first section, we should implement cable corridors to reduce instances of accidental disruption and make it more challenging to obfuscate sabotage operations. But this must be supported by robust monitoring and oversight of shipping activity within or adjacent to these corridors. Many ships are already required to use AIS (Automatic Identification System) technology to show their location, but enforcement is relatively weak. Better enforcement of the use of AIS can increase the security of subsea cables by enabling active monitoring, the use of alert systems, and accessing historical data in the event of cable disruption. The intentional concealment of repairs vessels’ location data, including Chinese ships, is already happening. Enforcement of AIS usage must keep pace to deter sabotage operations, with an awareness that AIS data can be spoofed.
Authors

Senior Director, Global Security and Technology Strategy, Venable LLP


Wahba Institute for Strategic Competition
The Wahba Institute for Strategic Competition works to shape conversations and inspire meaningful action to strengthen technology, trade, infrastructure, and energy as part of American economic and global leadership that benefits the nation and the world. Read more

Explore More
Browse Insights & Analysis
Optical Core Infrastructure: The Hidden Highway of Connectivity

Funding Infrastructure Requires More…of Everything


